고정 헤더 영역
상세 컨텐츠
본문
Credits This is your credit balance. Even if you are an anonymous user, you are given some credits to spend.
Every IP address has its own account and it is provided with free credits that can be used to pay for Online Domain Tools services. Moreover, credit balance is reset every day.
Aes Crypt Software
This is why we call them Daily Credits. Registered users have higher Daily Credits amounts and can even increase them by purchasing subscriptions. Besides Daily Credits, all accounts, including IP address accounts of anonymous users, have their credit Wallet. Wallet credits are not reset on a daily basis, but they are only spent when a user has not enough Daily Credits. Registered users can buy credits to their wallets.
All IP address accounts are created with an initial Wallet balance of 3.00. Once IP address account spends credits from its Wallet, it can not be charged again. This should allow new users to try most of Online Domain Tools services without registration. Checkout The table in Checkout section clearly summarizes prices that are associated with options you choose in the tool's form. Your credit balance is displayed on the right side above the main menu. Even if you are an anonymous user, you are given some credits to spend. Every IP address has its own account and it is provided with free credits that can be used to pay for Online Domain Tools services.
Moreover, credit balance is reset every day. This is why we call them Daily Credits. Accounts of registered users have higher Daily Credits amounts and can even increase them by purchasing subscriptions. Besides Daily Credits, all accounts, including IP address accounts of anonymous users, have their credit Wallet. Wallet credits are not reset on a daily basis, but they are only spent when a user has not enough Daily Credits. Registered users can buy credits to their wallets. All IP address accounts are created with an initial Wallet balance of 3.00.
Once IP address account spends credits from its Wallet, it can not be charged again. This should allow new users to try most of Online Domain Tools services without registration. Symmetric Ciphers Online allows you to encrypt or decrypt arbitrary message using several well known such as AES, 3DES, or BLOWFISH. Symmetric ciphers use the same (or very similar from the algorithmic point of view) keys for both encryption and decryption of a message.
They are designed to be easily computable and able to process even large messages in real time. Symmetric ciphers are thus convenient for usage by a single entity that knows the secret key used for the encryption and required for the decryption of its private data – for example file system encryption algorithms are based on symmetric ciphers. If symmetric ciphers are to be used for secure communication between two or more parties problems related to the management of symmetric keys arise. Such problems can be solved using a that includes using.
Symmetric ciphers are basic blocks of many cryptography systems and are often used with other cryptography mechanisms that compensate their shortcomings. Symmetric ciphers can operate either in the or in the. Some algorithms support both modes, others support only one mode. In the block mode, the cryptographic algorithm splits the input message into an array of small fixed-sized blocks and then encrypts or decrypts the blocks one by one. In the stream mode, every digit (usually one bit) of the input message is encrypted separately. In the block mode processing, if the blocks were encrypted completely independently the encrypted message might be vulnerable to some trivial attacks. Obviously, if there were two identical blocks encrypted without any additional context and using the same function and key, the corresponding encrypted blocks would also be identical.
This is why block ciphers are usually used in various. Operation modes introduce an additional variable into the function that holds the state of the calculation. The state is changed during the encryption/decryption process and combined with the content of every block. This approach mitigates the problems with identical blocks and may also serve for other purposes.
The initialization value of the additional variable is called the. The differences between block ciphers operating modes are in the way they combine the state (initialization) vector with the input block and the way the vector value is changed during the calculation. The stream ciphers hold and change their internal state by design and usually do not support explicit input vector values on their input. Using the Input type selection, choose the type of input – a text string or a file. In case of the text string input, enter your input into the Input text textarea 1,2. Otherwise, use the 'Browse' button to select the input file to upload. Then select the cryptographic function you want to use in the Function field.
Depending on the selected function the Initialization vector (IV) field is shown or hidden. Initialization vector is always a sequence of bytes, each byte has to be represented in hexadecimal form. Select the operation mode in the Mode field and enter a key in the Key field. The permitted lengths of keys for particular cryptographic functions are listed below. If you don't specify a key with permitted length the key is prolonged with the proper number of null bytes at the end. When the key is changed the prefix of sha1(key) function is automatically filled in the IV field.
You still may change the IV. The feature is intended only for your convenience. Using the radio buttons under the Key input field, you can specify whether the entered key value should be interpreted as a plain text or a hexadecimal value. Finally, click the 'Encrypt!' Button or the 'Decrypt!'
Button depending on whether you want the input message to be encrypted or decrypted. The output message is displayed in a hex view and can also be downloaded as a binary file. The format of output file is simply a dump of binary data.
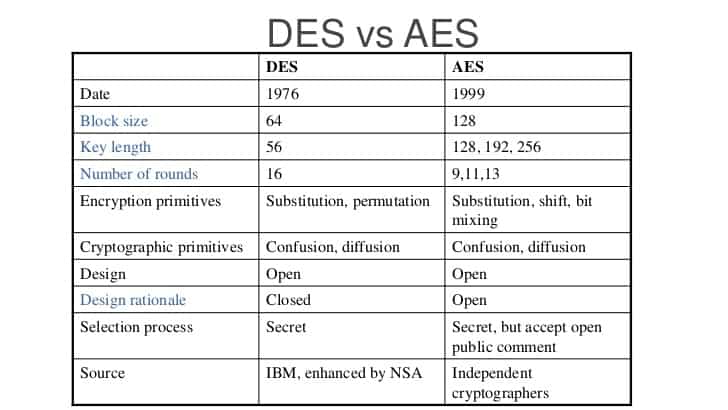
The initialization vector is added to the file name for convenience. Cryptographic function Key lengths Initialization vector lengths (all modes) In bytes In bits In bytes In bits AES 16, 24 or 32 128, 192 or 256 16 128 DES 1 to 8 bytes 8 to 64 16 128 TRIPLEDES 1 to 24 8 to 192 16 128 BLOWFISH 1 to 56 8 to 448 16 128 BLOWFISH-compat 1 to 56 8 to 448 16 128 RIJNDAEL-256 1 to 32 8 to 256 64 512 R4 1 to 256 8 to 2048 -SERPENT 1 to 32 8 to 256 32 256 TWOFISH 1 to 32 8 to 256 32 256 Table 1. Supported key lengths and IV lengths 1 You can use only hexadecimal characters, newlines, tabulators and new line characters if you decrypt a string.
2 Input text has an autodetect feature at your disposal. The autodetect detects for you if the content of Input text field is in form of a plain text or a hexadecimal string.
You can turn off the feature by clicking on 'OFF' or by changing current type of input under the Input text field.
An inportant note is that the GUI applicaton is actually a script that executes the command-line version created for the Mac. To install the GUI application, just Click on the 'AESCrypt' package and follow the prompts. The best way to use the tool is to drag the AESCrypt application to the Dock and drop files to be encrypted on it.
To decrypt, find the file in the same directory where the original file was located, which will have an AESCrypt Icon associated with it and double click it. Command-Line Option The Mac version of AES Crypt was created from the source code created for Linux.
It works exactly like the Linux version. So, rather than repeating much or all of the same information, please refer to the page for examples of how to use AES Crypt on the Mac. For those who wish to compile your own binaries, all you need to do is install the development tools and type 'make'. Apple could not have made it any simpler.




